Cybersecurity is a rapidly growing field, with the global cybersecurity market projected to reach $500 billion by 2030 (Source: Fortune Business Insights). This growth creates numerous opportunities for learners and professionals to develop their skills through hands-on projects. We will check 50 Cyber Security Projects,
Whether you’re a beginner looking to understand the basics or an expert seeking advanced challenges, there’s always a new area to explore, such as AI-driven security, zero-trust architectures, and quantum cryptography.
Here, we’ve compiled 50 cybersecurity project ideas that can help you gain practical experience and enhance your problem-solving skills.
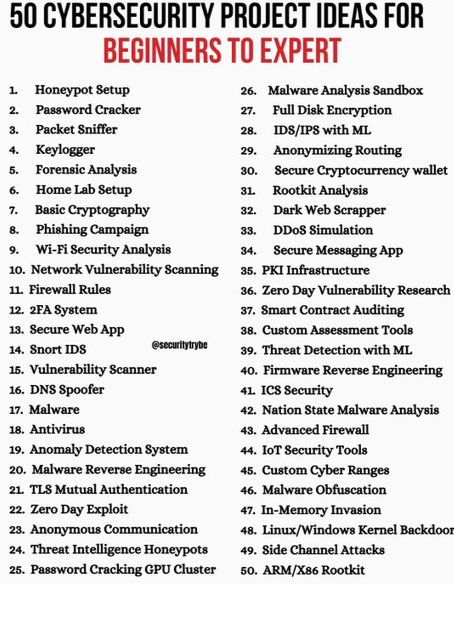
50 Cyber Security Projects
🔐 Beginner-Level Cybersecurity Projects for Beginners
If you’re new to cybersecurity, these beginner-friendly projects will help you build foundational skills in networking, cryptography, ethical hacking, and cyber forensics. Working hands-on with real tools is the best way to strengthen your understanding of cybersecurity fundamentals and prepare for more advanced challenges.
1. Honeypot Setup – Deploy a honeypot to lure and analyze cyber threats.
A honeypot is a decoy system used to attract hackers, allowing you to observe real-world cyber attacks safely. Setting up a honeypot helps you understand network intrusion methods, malware behavior, and how to detect suspicious activity. This project is ideal for learning network monitoring and threat intelligence.
2. Password Cracker – Create a tool that can test password strength using brute-force or dictionary attacks.
This project helps you learn how password security works by building a tool that simulates how attackers try to crack weak passwords. It’s a safe way to understand brute-force attacks, hashing, and why strong password policies are crucial in cybersecurity.
3. Packet Sniffer – Develop a simple tool to monitor and analyze network traffic.
Building a packet sniffer teaches you how to capture and study data packets traveling across a network. You’ll gain hands-on experience with network protocols, data transmission, and traffic analysis—key skills for anyone pursuing network security.
4. Keylogger – Understand how keyloggers work by building a basic one for educational purposes.
This project introduces you to how keylogging software captures keystrokes. You’ll learn about endpoint security, data privacy, and methods to detect and prevent keyloggers in real-world systems. Always conduct this project ethically in a controlled lab environment.
5. Forensic Analysis – Conduct digital forensics on a sample system to investigate a cyber incident.
Learn how to perform digital forensics by analyzing a compromised system. You’ll practice identifying traces of malicious activity, collecting evidence, and building an investigation report essential for careers in cyber incident response and digital forensics.
6. Home Lab Setup – Set up a virtual cybersecurity lab for testing and learning.
Creating your own cybersecurity home lab using virtual machines allows you to experiment safely with tools like Wireshark, Metasploit, and Nmap. It’s the perfect environment for practicing ethical hacking and testing network vulnerabilities without risk.
7. Basic Cryptography – Implement encryption and decryption techniques for securing data.
Understanding cryptography is vital in cybersecurity. In this project, you’ll implement basic encryption algorithms like Caesar cipher or AES to protect data. It helps you grasp how data confidentiality and secure communication work in modern systems.
8. Phishing Campaign – Simulate a phishing attack to understand how social engineering works.
By designing a phishing simulation, you’ll see firsthand how social engineering tricks users into revealing sensitive information. This project teaches you to identify phishing emails, craft security awareness campaigns, and strengthen human-layer security.
9. Wi-Fi Security Analysis – Analyze and secure wireless networks against potential threats.
Performing a Wi-Fi security audit helps you understand how wireless networks can be exploited. You’ll test encryption standards, identify vulnerabilities, and learn techniques to protect home and corporate Wi-Fi networks from attackers.
10. Network Vulnerability Scanning – Use tools like Nmap or Nessus to identify vulnerabilities.
Using vulnerability scanners such as Nmap or Nessus helps you detect weaknesses in a system or network. This project enhances your skills in network mapping, port scanning, and risk assessment, essential steps in proactive cyber defense.
Intermediate-Level Cybersecurity Projects
Intermediate-Level Cybersecurity Projects
If you’ve already mastered the basics, these intermediate cybersecurity projects will take your skills to the next level. They focus on advanced security concepts, penetration testing techniques, and real-world defensive strategies used by professionals. Working on these projects helps bridge the gap between beginner labs and advanced cybersecurity certifications.
11. Firewall Rules – Configure firewalls to protect networks from unauthorized access.
This project helps you learn how to create, manage, and test firewall rules that control inbound and outbound traffic. By configuring firewalls like pfSense or iptables, you’ll understand how to block malicious traffic, whitelist trusted connections, and strengthen network perimeter security.
12. 2FA System – Implement two-factor authentication for secure login systems.
Build a two-factor authentication (2FA) system to enhance login security using methods like SMS, email OTPs, or authenticator apps. This project teaches you about multi-factor authentication protocols, user verification, and how to prevent unauthorized access to systems or web applications.
3. Secure Web App – Develop a web application with robust security measures.
Design a secure web application while implementing best practices for web application security such as input validation, HTTPS, and secure session handling. You’ll learn about OWASP Top 10 vulnerabilities like SQL Injection, XSS, and CSRF—and how to prevent them through secure coding.
4. Snort IDS – Set up and configure Snort for intrusion detection.
Snort is an open-source Intrusion Detection System (IDS) widely used in cybersecurity. Setting it up allows you to monitor real-time network traffic, detect suspicious activity, and create custom alert rules. This project enhances your understanding of network monitoring and threat detection.
5. Vulnerability Scanner – Build a tool that detects security flaws in software or networks.
Developing your own vulnerability scanner helps you identify weaknesses in applications and systems. You’ll work with port scanning, banner grabbing, and exploit detection methods. This project builds a foundation for penetration testing and ethical hacking careers.
6. DNS Spoofer – Simulate DNS attacks to understand and prevent DNS hijacking.
By simulating DNS spoofing or DNS cache poisoning, you’ll see how attackers redirect users to fake websites. This project teaches you how to detect and prevent DNS-based attacks, implement DNSSEC, and secure your organization’s domain infrastructure.
7. Malware Analysis – Examine malware behavior using sandbox environments.
In this project, you’ll safely execute malware samples inside a sandbox environment to study their behavior. You’ll learn about malware signatures, process injection, and network indicators of compromise (IOCs) — vital skills for anyone interested in cyber threat analysis or incident response.
8. Antivirus – Develop a simple antivirus scanner to detect malicious files.
Create a basic antivirus program that scans files and detects known threats based on hash signatures or heuristic rules. This project strengthens your knowledge of malware detection, file integrity monitoring, and how antivirus engines identify suspicious patterns.
9. Anomaly Detection System – Create a system that detects unusual patterns in network traffic.
Using techniques like machine learning or statistical analysis, build an anomaly detection system to identify irregular activity that might signal a cyberattack. You’ll learn about behavioral analytics, AI-driven cybersecurity, and threat prediction models used in modern SOCs (Security Operations Centers).
10. Malware Reverse Engineering – Analyze malicious software to understand its behavior and impact.
This advanced project involves reverse engineering malware using tools like Ghidra or IDA Pro to dissect malicious code and study its structure. You’ll uncover how malware evades detection, exploits systems, and affects files — key insights aligned with NIST Malware Analytics best practices.
Read on to learn how to choose a Quantitative research topic
Advanced-Level Cybersecurity Projects
For cybersecurity enthusiasts looking to push their limits, these projects involve sophisticated attack simulations, advanced encryption, and malware development.
- TLS Mutual Authentication – Implement mutual TLS for secure communication between clients and servers.
- Zero Day Exploit – Research and simulate zero-day vulnerabilities.
- Anonymous Communication – Build a secure communication system that ensures anonymity.
- Threat Intelligence Honeypots – Design honeypots that collect real-world cyber threat data.
- Password Cracking GPU Cluster – Use GPU acceleration to crack passwords efficiently.
- Malware Analysis Sandbox – Create an isolated environment for analyzing malware behaviour.
- Full Disk Encryption – Implement encryption solutions for securing entire disks.
- IDS/IPS with ML – Develop an intrusion detection/prevention system powered by machine learning.
- Anonymizing Routing – Implement Tor-like routing for private communication.
- Secure Cryptocurrency Wallet – Design a secure cryptocurrency wallet with multi-factor authentication.
- Rootkit Analysis – Study and analyze rootkits to understand how they evade detection.
- Dark Web Scraper – Build a tool to scrape and analyze content from the dark web.
- DDoS Simulation – Simulate and analyze distributed denial-of-service attacks.
- Secure Messaging App – Develop an end-to-end encrypted messaging application.
- PKI Infrastructure – Implement Public Key Infrastructure for secure communications.
- Zero Day Vulnerability Research – Identify and analyze unknown vulnerabilities in software.
- Smart Contract Auditing – Review and secure blockchain-based smart contracts.
- Custom Assessment Tools – Build tools to evaluate the security posture of systems.
- Threat Detection with ML – Use machine learning to identify and prevent cyber threats.
- Firmware Reverse Engineering – Analyze and reverse-engineer firmware for security analysis.
- ICS Security – Secure industrial control systems from cyber threats.
- Nation-State Malware Analysis – Investigate and study nation-state-sponsored malware campaigns.
- Advanced Firewall – Develop a firewall with custom rule sets and detection mechanisms.
- IoT Security Tools – Build security tools to protect Internet of Things (IoT) devices.
- Custom Cyber Ranges – Create a controlled environment for testing security scenarios.
- Malware Obfuscation – Design techniques to evade malware detection systems.
- In-Memory Invasion – Study memory-based attack techniques and their countermeasures.
- Linux/Windows Kernel Backdoor – Analyze kernel-level backdoors and security implications.
- Side Channel Attacks – Investigate and demonstrate attacks that exploit physical hardware vulnerabilities.
- ARM/X86 Rootkit – Develop and study rootkits targeting ARM and X86 architectures.
Final Thoughts
Cybersecurity is an ever-evolving field that requires continuous learning and hands-on experience. According to a 2023 Cybersecurity Ventures report, there is an estimated global shortage of 3.5 million cybersecurity professionals, making skill development more critical than ever.
Whether you’re just starting or are an experienced security researcher, these projects will help you develop the skills needed to tackle real-world cyber threats. Start with beginner projects, move to intermediate challenges, and finally, take on advanced topics to become a cybersecurity expert!
Are you working on a cybersecurity project? Share your experience in the comments below! What challenges have you faced, and what tools have you found most useful?









 Evan John
Evan John