In the realm of software development, protecting intellectual property and sensitive algorithms from prying eyes is a constant challenge. Hackers and malicious entities are constantly seeking ways to reverse engineer software to exploit vulnerabilities or steal valuable information. To counter these threats, software protection mechanisms are implemented to make it difficult for unauthorized individuals to understand the underlying code and algorithms. One such mechanism is obfuscation, which aims to transform the code into a complex and unintelligible form without altering its functionality.
Understanding Software Protection
Software protection refers to the various techniques and measures implemented to safeguard software applications from unauthorized access, modification, and distribution. It involves a combination of encryption, access control, and obfuscation techniques to ensure the security and integrity of the software. By employing software protection mechanisms, developers can deter potential attackers and reduce the risks associated with unauthorized use or manipulation of their software.
The Need for Obfuscation
Obfuscation plays a vital role in software protection by making the code harder to understand, analyze, and reverse engineer. It involves transforming the code in such a way that it becomes difficult for attackers to extract meaningful information from it. Obfuscation techniques include code obfuscation, data obfuscation, and control flow obfuscation, among others. These techniques introduce complexity and confusion into the code, making it challenging for attackers to comprehend the logic and purpose of the software.
Read on Best Computer Science Assignment Help
What is Distributed Obfuscation?
Distributed obfuscation is an innovative approach to software protection that leverages the power of distributed systems and cloud computing. In this model, the obfuscation process is performed across multiple nodes or machines, making it even more challenging for attackers to decipher the obfuscated code. By distributing the obfuscation tasks, the computation becomes more resource-intensive, time-consuming, and complex, adding an extra layer of protection to the software.
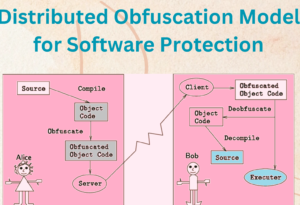
Key Components of a Distributed Obfuscation Model
A distributed obfuscation model consists of several key components:
- Obfuscation Engine: The core component responsible for performing the obfuscation tasks across multiple nodes or machines.
- Task Distribution: Mechanisms for distributing the obfuscation tasks among the nodes, ensuring an efficient utilization of resources.
- Code Segmentation: Breaking down the code into smaller segments to distribute the obfuscation process effectively.
- Communication Infrastructure: A robust network infrastructure to facilitate communication and coordination among the distributed nodes.
- Obfuscation Parameters: Configurable parameters that control the level of obfuscation applied to the software.
Working Principle of Distributed Obfuscation
The working principle of a distributed obfuscation model involves the following steps:
- Code Segmentation: The original code is divided into smaller segments to distribute the obfuscation tasks across multiple nodes.
- Task Distribution: The obfuscation tasks are assigned to different nodes, leveraging their computing power and resources.
- Obfuscation Process: Each node performs obfuscation on its assigned code segment, applying various obfuscation techniques.
- Code Reassembly: The obfuscated code segments are collected and reassembled to generate the final obfuscated software.
- Deploying Obfuscated Software: The obfuscated software is deployed, providing enhanced protection against reverse engineering and unauthorized access.
Benefits of Distributed Obfuscation
Implementing a distributed obfuscation model offers several benefits:
- Enhanced Security: Distributed obfuscation adds an extra layer of complexity and confusion to the software, making it significantly harder for attackers to reverse engineer or understand the code.
- Improved Scalability: By leveraging distributed systems, the obfuscation process can be parallelized and scaled to handle large software applications effectively.
- Resource Utilization: Distributing the obfuscation tasks among multiple nodes ensures efficient utilization of computing resources and reduces the time required for obfuscation.
- Resilience to Attacks: The distributed nature of the obfuscation process makes it more resilient to attacks, as compromising a single node does not reveal the complete obfuscation logic.
- Future-proofing: As computing power continues to advance, distributed obfuscation models can adapt and leverage the increased resources, ensuring the effectiveness of software protection mechanisms.
Check on Sample paper
Challenges and Limitations
While distributed obfuscation offers significant advantages, it also presents challenges and limitations:
- Increased Complexity: The distributed nature of obfuscation introduces additional complexity in terms of task distribution, communication, and synchronization.
- Resource Requirements: Implementing a distributed obfuscation model may require a substantial amount of computational resources, especially for large-scale software applications.
- Overhead and Latency: The communication overhead and latency among distributed nodes can impact the overall performance and responsiveness of the obfuscation process.
- Maintenance and Updates: Managing and maintaining a distributed obfuscation infrastructure requires careful attention to ensure its continued effectiveness and compatibility with evolving software.
Future Implications and Potential Applications
The distributed obfuscation model holds promising implications for the future of software protection. As computing power and cloud technologies advance, distributed obfuscation can become an integral part of software development practices. It has the potential to protect sensitive algorithms, intellectual property, and valuable trade secrets across various domains, including:
- Mobile Applications: Protecting mobile applications against reverse engineering and unauthorized access.
- IoT Devices: Safeguarding the firmware and software running on Internet of Things (IoT) devices from tampering and exploitation.
- Cloud-based Software: Ensuring the security and integrity of software deployed on cloud platforms.
- Digital Rights Management: Preventing unauthorized copying, distribution, and modification of copyrighted software.
Conclusion
In conclusion, the distributed obfuscation model offers a robust and effective solution for software protection in the face of evolving threats. By leveraging distributed systems and cloud computing, software developers can enhance the security and integrity of their applications. Distributed obfuscation adds complexity, confusion, and resilience to reverse engineering attempts, making it significantly harder for attackers to compromise the software. As technology advances, distributed obfuscation is poised to become an essential component of software protection strategies, providing a shield against unauthorized access and intellectual property theft.
FAQs









 Micheal Daniel
Micheal Daniel